One Day, Satoshi's Coins Will Move
Given enough time, quantum computing, or some other technological breakthrough will eventually crack the cryptography which secures Satoshi's coins...we need to think about how we handle this.
G’day Folks,
The quantum computing threat is one of the biggest pieces of legitimate FUD for Bitcoin, and it is a topic which has rightfully received more discussion of late.
Many subscribers have asked me to cover this topic, and I have had this piece sitting in my drafts folder for too many months now, slowly adding research to it over time.
Given the complexity of the topic at hand, it has taken me a while to fully consolidate my own thoughts, and to distil how I wanted to tackle the quantum problem. Even then, I strongly suspect this will only be my first piece of this subject, and my thoughts are likely to evolve as the research and debate progresses in the months ahead.
At some stage in the future, Satoshi’s approximately 1.1M BTC will move, or at least ‘change state’, and there are three primary ways this can happen;
Satoshi (or their descendants) spend them.
Quantum (or some other novel) computing advances enough to crack the cryptography to steal them.
The Bitcoin network implements a consensus code change which burns them.
Importantly, Satoshi’s coins are not the only ones at risk, and there are other attack vectors such as many lost coins, coins held in re-used addresses, and sniping transactions in the mempool which can affect all of us.
In this piece, I want to share my current thinking around the quantum computing subject, specifically focusing on topics related to the vulnerable supply:
My current understanding of the various quantum attack vectors and threats.
The number of coins which are likely to be vulnerable to a quantum attack.
The risk of address re-use, particularly amongst large custodians and exchanges.
My opinion on how I think the Bitcoin network should handle these ‘at-risk’ coins.
The quantum computing threat is anything but a simple topic, however I also believe there is a relatively pragmatic way to break the problem down into bite sized pieces.
By the end of this piece, I hope readers will have a much clearer view on the risks quantum computing poses to Bitcoin, and be able to better reason about the next steps.
Premium Members will find the TL:DR summary, video update and the rest of the written post below. Consider upgrading to premium today to unlock the rest of the content!
Disclaimer: This article is general in nature, and is for informational, and entertainment purposes only, and it shall not be relied upon for any investment or financial decisions.
TL;DR Summary
The quantum threat to Bitcoin is hard to handicap, but I am seeing enough smart and credible people suggesting it is real, and likely on the horizon for the next decade (Q-day somewhere in 2030-2035).
The majority of Bitcoin is currently quantum safe, and the coins you hold in your wallet will not be vulnerable to theft assuming the following:
You do not re-use addresses, and treat all addresses as one-time-use (if you do re-use, it is time to upgrade your security practices). Most wallets already generate a new address for you by default, making it standard practice.
Your coins are held in modern SegWit addresses starting with ‘bc1q’. Technically speaking older legacy addresses starting with ‘3’ are safe too, but most wallet software has deprecated these formats.
There are three main buckets of coins vulnerable to quantum theft:
1.72M BTC in Satoshi Era P2PK addresses, which are very likely lost, and thus at a high risk of quantum theft.
184k BTC in modern Taproot addresses, which is 1% of the supply, but the owners are likely to be active and can therefore upgrade.
I estimate 2% to 5% of the supply (365k to 914k BTC) is held in re-used addresses that are likely to be lost and unable to upgrade.
There is a much larger pool of 2.798M BTC in re-used addresses, however these are either active, or associated with exchanges and custodians. In both instances, the owning entity has the capacity to upgrade to quantum-safe practices over time.
Globally, I estimate there are between 2.08M ($187B) and 2.63M ($237B) vulnerable and lost BTC, equivalent to 3x to 4x Strategy Treasuries.
There is also a debate around whether we freeze/burn these vulnerable coins, or allow the law of the jungle to apply (we do nothing to these vulnerable coins, and they become fair game for whomever has access to the private key). Both have valid principles as the foundation, however I find myself opposed to the burning idea.
I am much more in favour of a rate-limiting hourglass approach that constrains the movement of P2PK coins to say 1-per-block (in line with the rest of the upgrade timeline, and much more than actual daily spends today).
The most important critical path, is focusing on developing quantum safe address types (perhaps those being worked on in BIP-360) to give Bitcoiners a choice to upgrade. The question of what we do with vulnerable lost supply, is then secondary once we have the options in place.
Full Premium Video
Prologue
I don’t plan to explore the deep dark details of how QC works, frankly because I would be lying to say I understand much of it.
With that said, the more time I have spent thinking through the QC problem, the more I came to realise that we probably don’t need to fully understand how QC works in order to reason about the risks and solution pathways pertaining to Bitcoin.
The short story is, a malicious actor with a cryptographically relevant quantum computer (CRQC) has the capacity to crack the signature of certain vulnerable coins, and steal them.
There is an entire debate surrounding whether quantum computing is actually a real and feasible technology, with many lumping it into the ‘it’s been 10-years away for the last 20-years’ bucket.
I’m not plugged in enough to handicap the probability of a CRQC coming to market. However, I have become aware of enough smart thinkers who are raising the alarm, and enough actions by governments and institutions to now consider it a real risk in the next 10yrs.
At a minimum, I am of the view that if we run the machine of human innovation long enough, we will eventually reach a state where some areas of Bitcoin’s underlying cryptography will be at risk, and therefore we must start thinking about this now.
There are several very useful references I found that are excellent sources of information for those looking to dive deeper into the technical details:
Chaincode Labs released a Bitcoin specific whitepaper in May 2025.
Nic Carter has written Part 1 on the QC technicals and Part 2 on the Bitcoin impact and reasons why he is advocating for near term action.
BIP-360 proposes a solution for a quantum resistant address format for Bitcoin, as well as plenty of logic for the risks and threats posed by QC.
Charles Edwards has been very vocal of late about the quantum threat to Bitcoin, and had a recent conversation with Preston Pysh sharing his views.
The Quantum Risk to Bitcoin
There are two primary risk vectors posed by QC to Bitcoin:
Theft of vulnerable coins using Shor’s algorithm. This is the primary risk we need to worry about, since the cryptography of Bitcoin’s signature schemes is by far the most vulnerable to QC. Coins at risk are those held in legacy addresses, taproot addresses, and re-used addresses.
Quantum mining using Grover’s algorithm. The breaking of SHA-256 is considerably more complex, and most analysts agree that the technology enabling quantum mining that out-competes ASICs is a considerable distance in the future (and thus I won’t focus on it in this piece).
✅️ Your coins are most likely safe. If you use modern Bitcoin wallets, and do not re-use addresses, your coins will most likely be safe and secure. The quantum threat is NOT something we need to panic about in the immediate term, and is instead a risk that may come to light several years down the road.
Bitcoin is a system that relies on cryptography, to provide asymmetric security assurances such that the only person who can spend coins locked to an address, is the one with the corresponding private key.
Some terminology:
Master Private Key (Seed Phrase) - This is your Bitcoin seed phrase, which is used to sign transactions and prove ownership of coins. It can derive an effectively infinite number of child private-public key pairs, which are then hashed into Bitcoin addresses.
Child Public-Private Key Pairs - These are mathematically derived from your master private key using elliptic curve cryptography (ECC). The child private key secures the child public key, and this public key can then be shared inside a Bitcoin transaction to prove and verify ownership to the network.
Addresses - A hashed form of the public key which is used as a human readable ‘destination’ for coins. Any coins sent to those addresses are then locked to the owner’s private key.
The critical part of this flow, is that with classical supercomputers, it would take trillions of years to reverse engineer a child private key from an exposed public key.
With CRQC’s, that assumption breaks down, and it would theoretically be possible for an exposed public key to be reverse engineered into a child private key.
It is really important to note that only the CHILD private key can be derived, not your master seed phrase, more on this shortly.
When Are Public Keys Exposed?
The primary risk for most Bitcoin holders, is that a CRQC can take an exposed public key, and derive the matching child private key.
To the best of my understanding, these are the main mechanisms whereby a public key would be exposed, thus making the coins held vulnerable to a CRQC:
Long-range attacks - Where a public key is exposed directly on the blockchain (e.g. via a mined transaction), and the QC attacker therefore has an infinite amount of time to work on back-calculating the child private key:
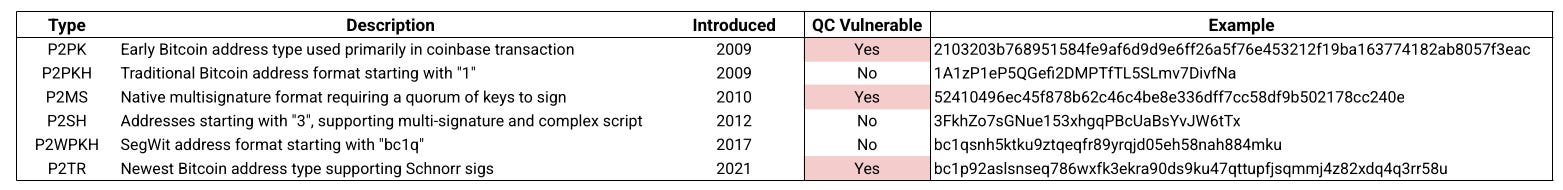
There are three Bitcoin address types which expose the public key by default and are therefore vulnerable at all times; P2PK (Satoshi era), P2MS (legacy multi-sig), and P2TR (Taproot).
Spending coins also exposes the public key, which makes any future coins held within re-used addresses vulnerable.
Whenever somebody exposes their extended public key (xpub), it makes all coins held within the children addresses vulnerable.
Short-range attacks - For any Bitcoin transaction, the public key is exposed whilst the coins are ‘in-flight’ in the mempool, and thus vulnerable. An attacker could effectively re-direct coins from their intended destination, to their wallet. This does mean that the time available for this kind of QC attack is much shorter (the ~10mins until the transaction is mined) and therefore it requires a considerably more powerful QC than is likely in the next decade.
The Layman’s Practical Summary
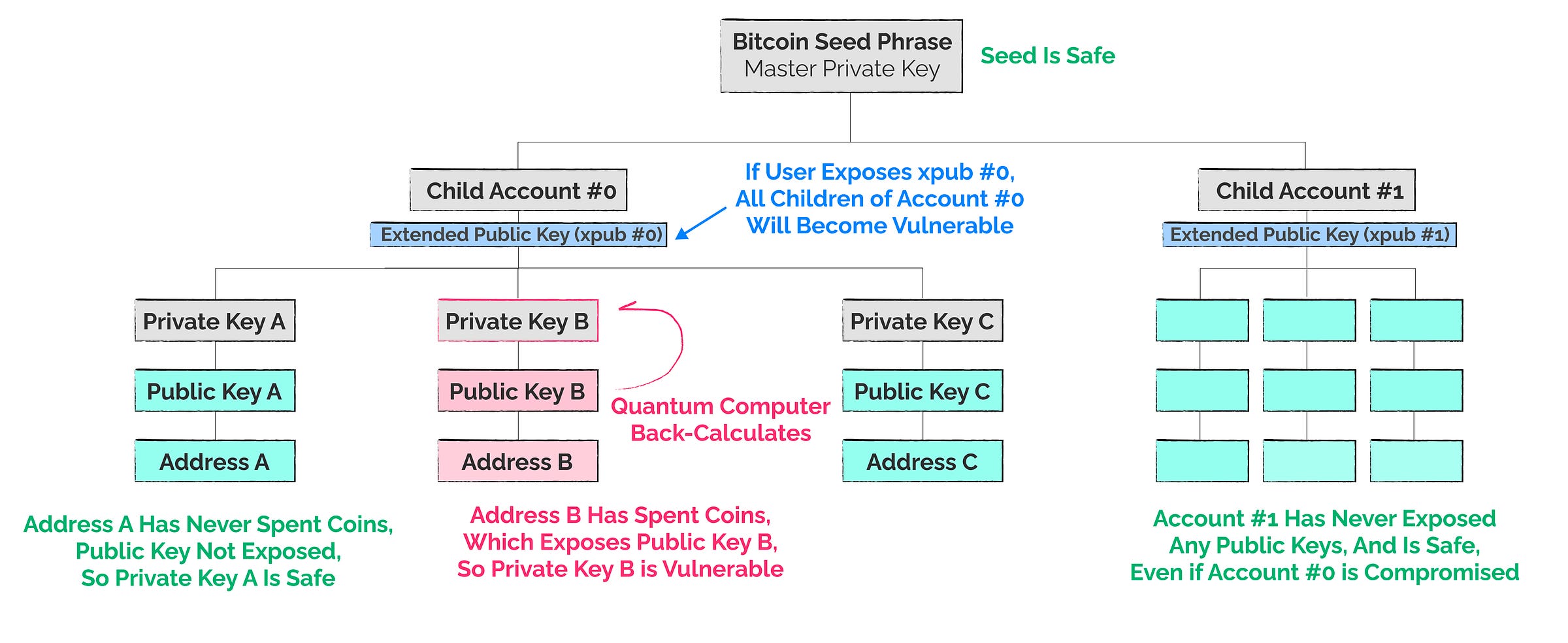
I know it can be very challenging to get your head around all this private-public key jargon, so I have constructed a diagram below showing my current understanding of the risks of a long-range attack.
The practical layman’s summary of the quantum risk for most Bitcoiners:
✅ Your Seed Phrase is safe - So long as you secure your seed phrase as usual, your master private key is safe from CRQCs.
✅ Unspent coins in a fresh address are safe - If you hold coins in a fresh one-time-use address, those coins are safe.
✅ Sub-accounts of your seed are safe - You can generate an infinite number of sub-accounts from your seed phrase, whether via an account number, or a passphrase.
✅ Wallets already use best practices - Almost all wallets will generate a fresh one-time use address for every coin received.
⛔️ Re-used addresses are vulnerable - once a coin has been spent from an address, it should not be used again, as that public key has been exposed.
⚠️ Accounts with exposed xpubs might be vulnerable - if your xpub has been exposed, all coins held in that child account will become vulnerable as it exposes all of the derived public keys.
A good example of a risk you may not think about, is if you use crypto-tax software, or an exchange API that tracks your xpub. These may become honeypots for hacks, and those xpubs effectively expose all public keys for that child wallet account.
⚠️ Transactions in the mempool are technically vulnerable, but not anytime soon. Whilst this is a risk, the truth is CRQCs capable of this attack are much further out, and even then, unless you’re moving around a few billion dollars worth of Bitcoin, you’re not going to be the target.
Ok, So How Many Coins Are At Risk?
We now have a general idea of the type of coins which are at quantum risk, and can now try and estimate the volumes of vulnerable supply:
Coins held in vulnerable address types.
Satoshi era coins held in legacy P2PK and P2MS addresses.
Modern coins held in P2TR Taproot addresses.
Coins held in re-used addresses, with a particular focus on those which appear to be lost or dormant.
Vulnerable Address Types
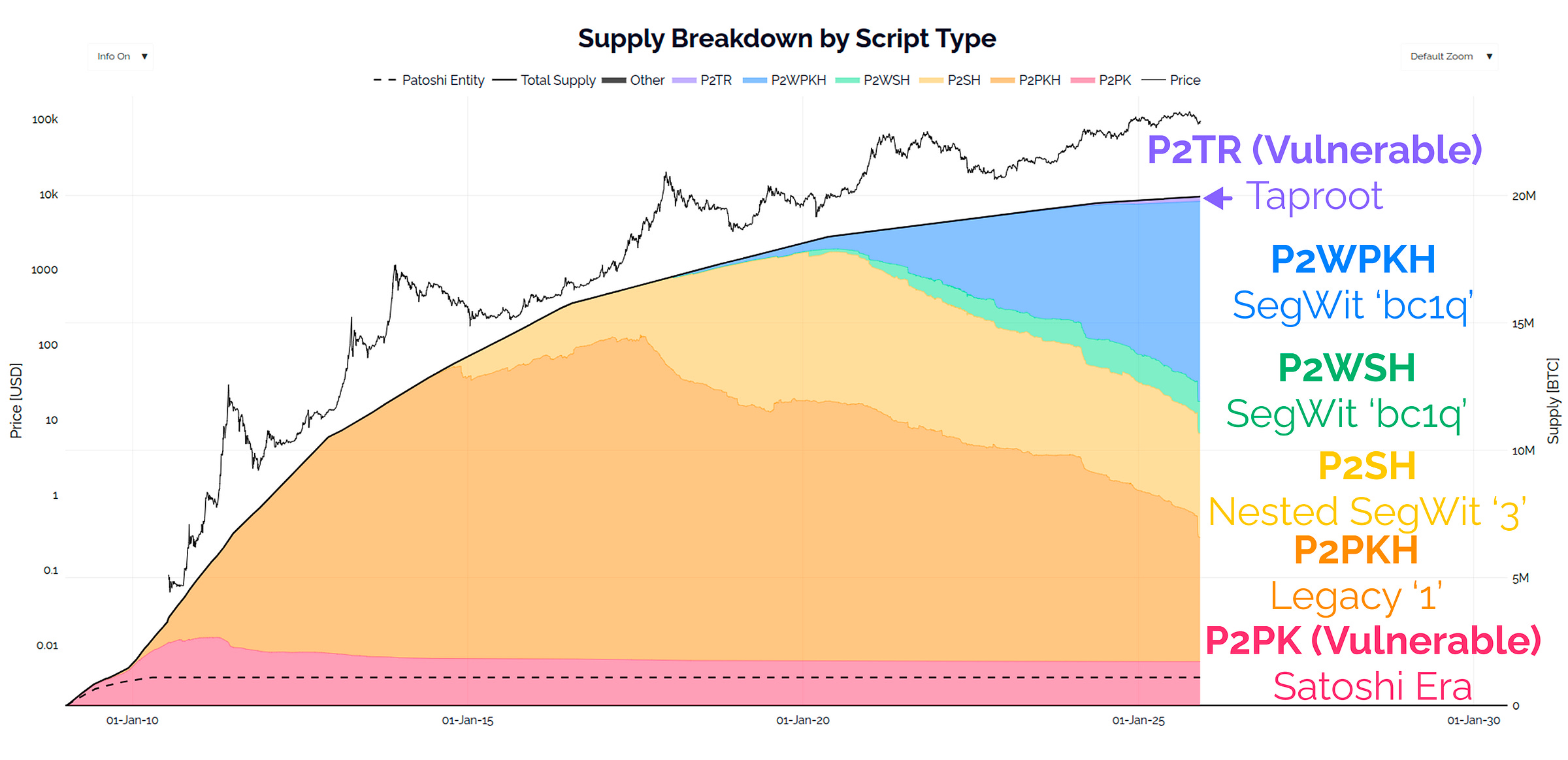
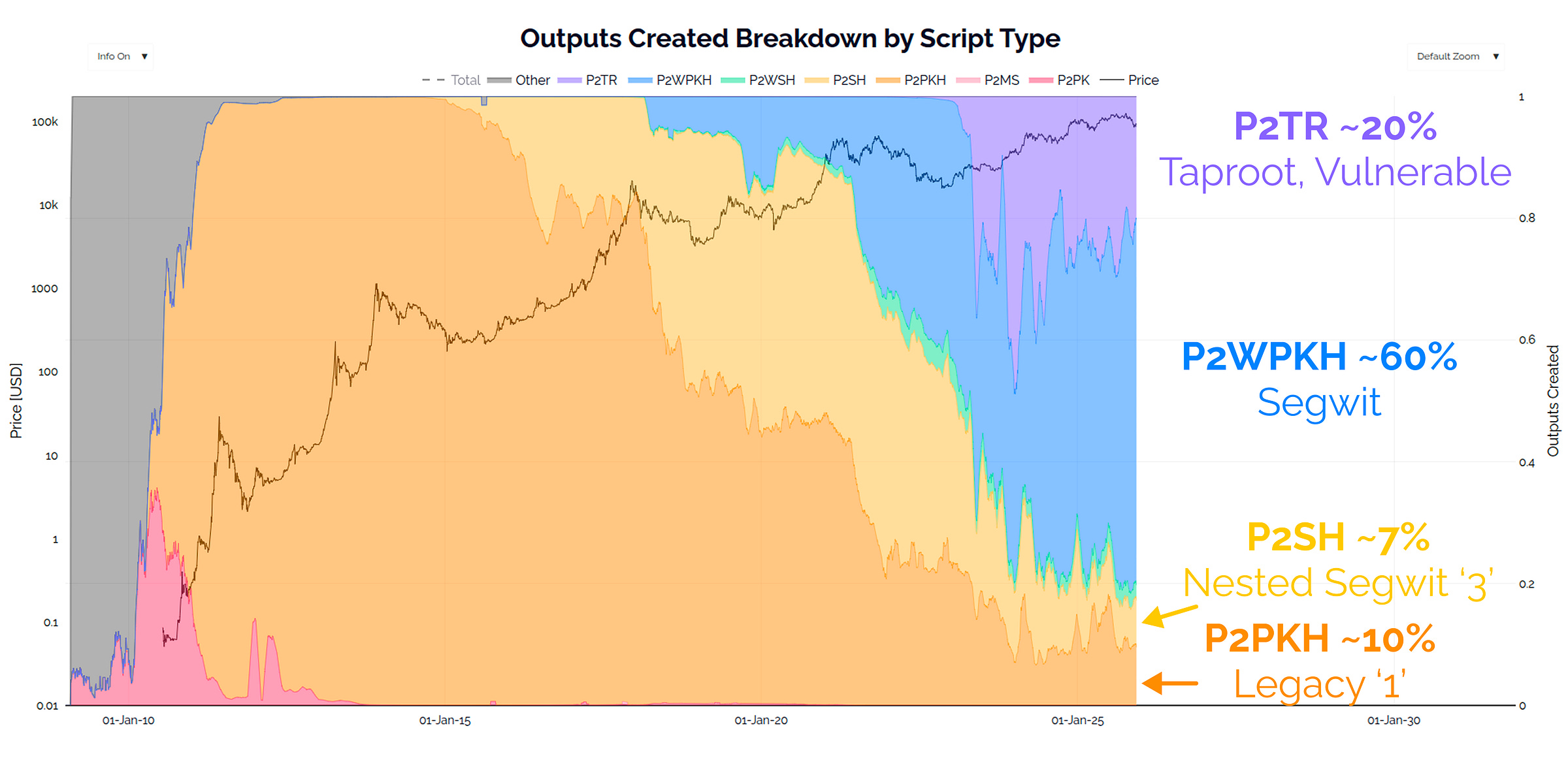
For the vast majority of our readers, unless you were around in the Satoshi era, you will likely never have used the early P2PK (red below), and P2MS (so small you can’t see it) address types. If your wallet shows your addresses start with either a ‘1’, ‘3’, or ‘bc1q’, then your coins are safe from any proximate quantum threat.
The P2MS multi-sig address type has seen limited usage, and currently holds a fairly negligible 69.66 BTC in total value, spread across 1.72M UTXOs.
For Taproot addresses (purple above), whilst they represent 34.3% of the UTXOs (55.4M in total), the total BTC held is relatively small at ~184k BTC, which is around 1% of the circulating supply. A primary reason for the huge UTXO count, but small supply held, is Taproot has been the preferred address type for users of ordinals, inscriptions and other arbitrary data, with most UTXOs holding a few thousand sats.
The Satoshi era P2PK address type (red above) however are of much more interest, as they represent the address type that Satoshi and other early pioneers used for their 50 BTC block rewards in the CPU mining era.
There are only 34,826 UTXOs that use P2PK, but they account for a massive 1.72M BTC, worth ~$155B at today’s prices (with an avg of 49.3 BTC per UTXO).
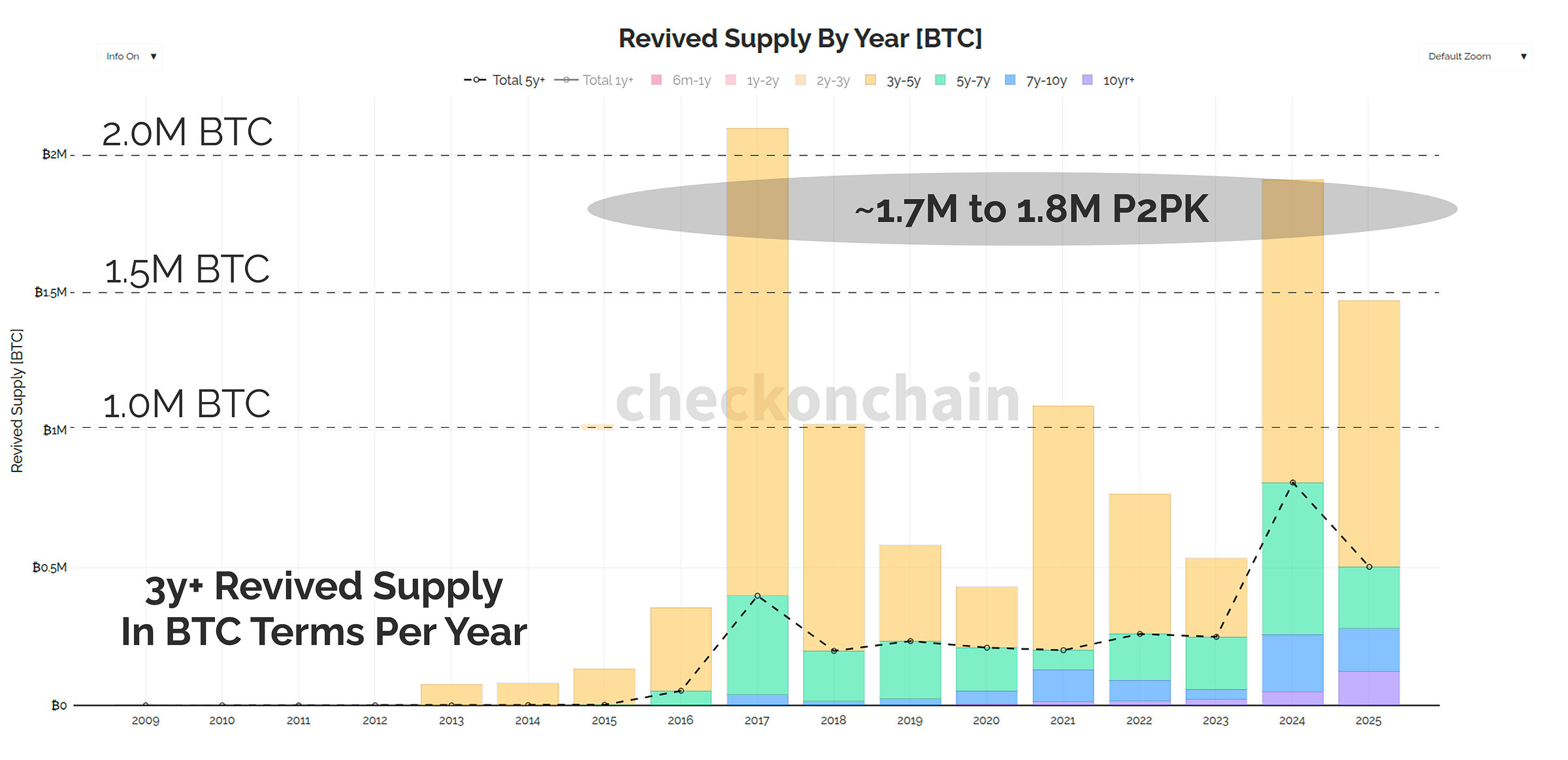
To give a sense of comparative scale, the chart below shows all the total revived supply for coins aged 3-years+ in each calendar year. We often consider this to be full cycle HODLers who are usually taking profit in bulls.
Should all of these 1.72M BTC P2PK coins be revived by a CRQC, it would amount to a full year of peak bull market profit taking like we saw in 2017, 2024 and 2025.
Check the HODLer: Whilst the market would certainly take time to digest such a cache of Bitcoin, I actually find this rather comforting, in that these ancient lost P2PK coins would be absorbed in a single year of bull market demand.
This also only compared to 3-year+ coins, which are typically around half of the total supply revived by Long-Term Holders.
Vulnerable Coins In Re-used Addresses
The second bucket of QC vulnerable coins, are those held in re-used addresses.
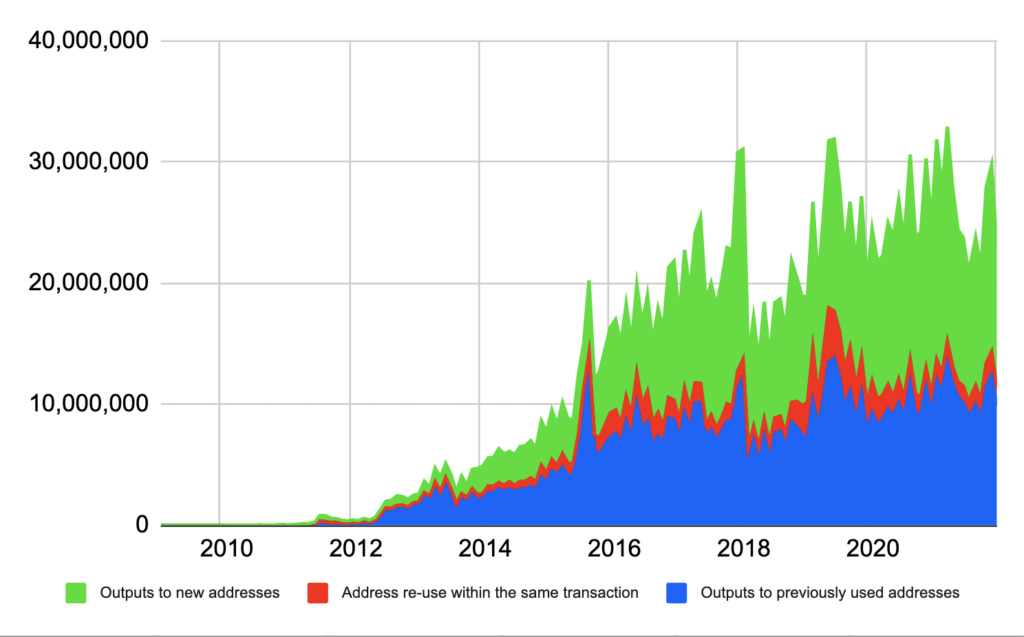
I actually found it quite difficult locating an up-to-date data source covering address re-use, but BitMex Research published a great report in 2022, which indicated around 50% of UTXOs are held by re-used addresses (blue and red).
Exchanges, and custodians are by far the biggest culprits here, as they often design their wallet infrastructure to spend in and out of the same set of hot/cold wallet addresses. They also have millions of customers depositing to what are usually static addresses.
The good news on this front, is that those exchanges and custodians also have a huge incentive to upgrade their wallet practices, whether by eliminating address re-use, or upgrading to a future quantum secure address format.
The bad news, is this will undoubtedly run into user experience issues, as many customers will fail to understand the risk, and continue re-using their existing deposit addresses. These exchanges may need to start prompting their customers to use a unique deposit address every time, and I pray for their customer service teams.
I do however find it highly unlikely that leadership, and the army of blockchain engineers who work for custodians like Binance and Coinbase are oblivious to the QC threat.
I mean…Ray Dalio was just on normie-vision CNBC talking about Bitcoin and QC…so it is reasonable to assume the smart folks over at Binance and Coinbase are well aware, and will have well developed post-quantum plans in the oven.
Whilst it is a somewhat crude approach, my high level strategy to study the risk of coins held in re-used addresses involved pulling the top 1000 Bitcoin ‘rich-list’ addresses, and then analysing the following questions:
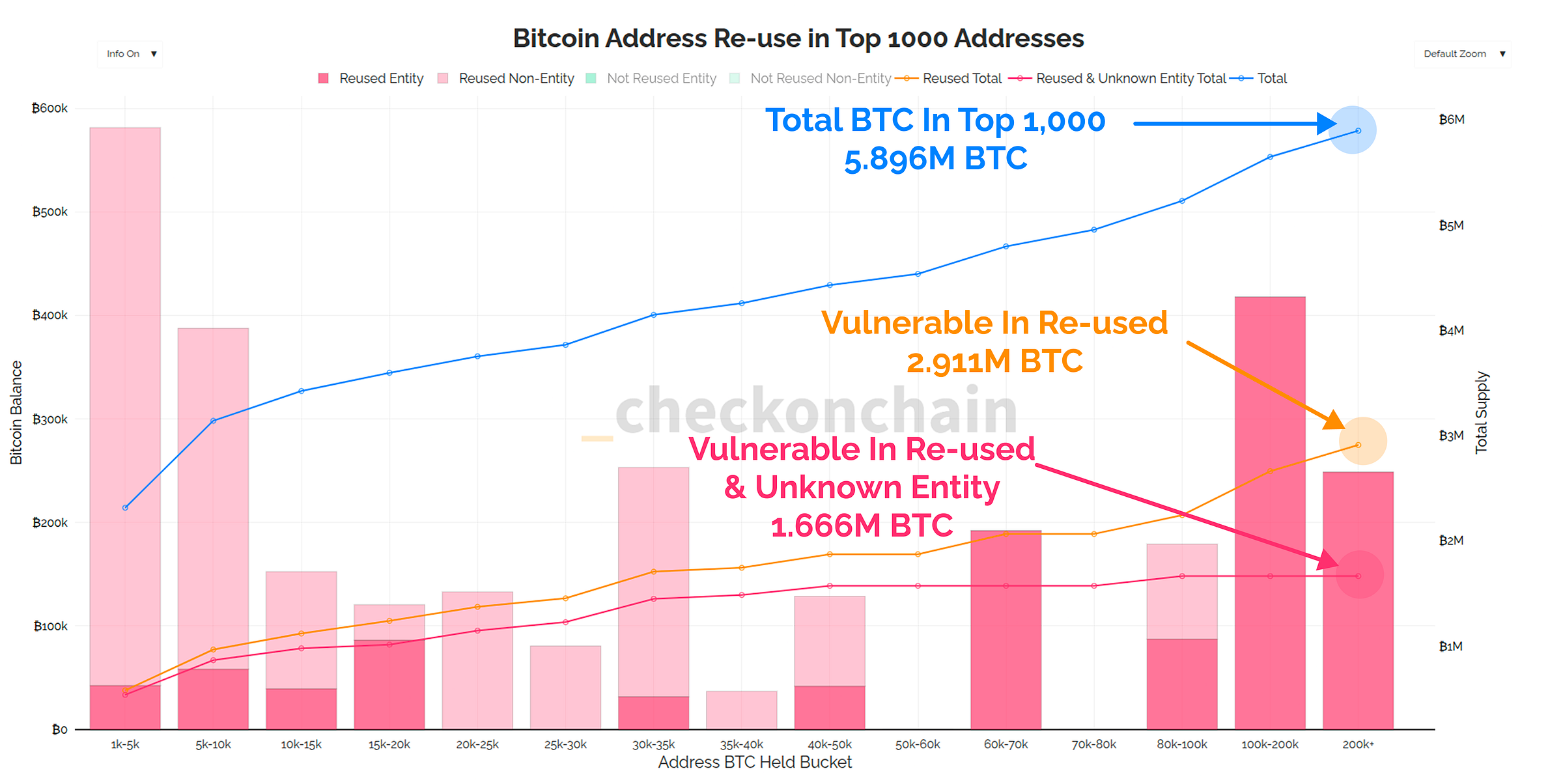
Out of the 5.896M BTC (~29.5% of circulating) held in the top 1000 addresses, how many are held in vulnerable re-used addresses?
How many of those re-used address coins are labelled as exchanges or custodians who have the capacity to upgrade to quantum safe practices (and thus represent lower risk)?
Of the remaining vulnerable re-use coins, how many look likely to be lost because they have not transacted in a very long time (and therefore represent a higher risk)?
This study showed that around 2.911M BTC, nearly half of the coins in the top 1,000 ‘rich list’, are held in vulnerable re-used addresses. By isolating labelled exchange entities, this breaks down further into:
1.245M BTC ($112B) held in re-used addresses, but owned by a labelled entity who can upgrade them.
1.666M BTC ($150B) held in re-used addresses, but without a corresponding exchange label.
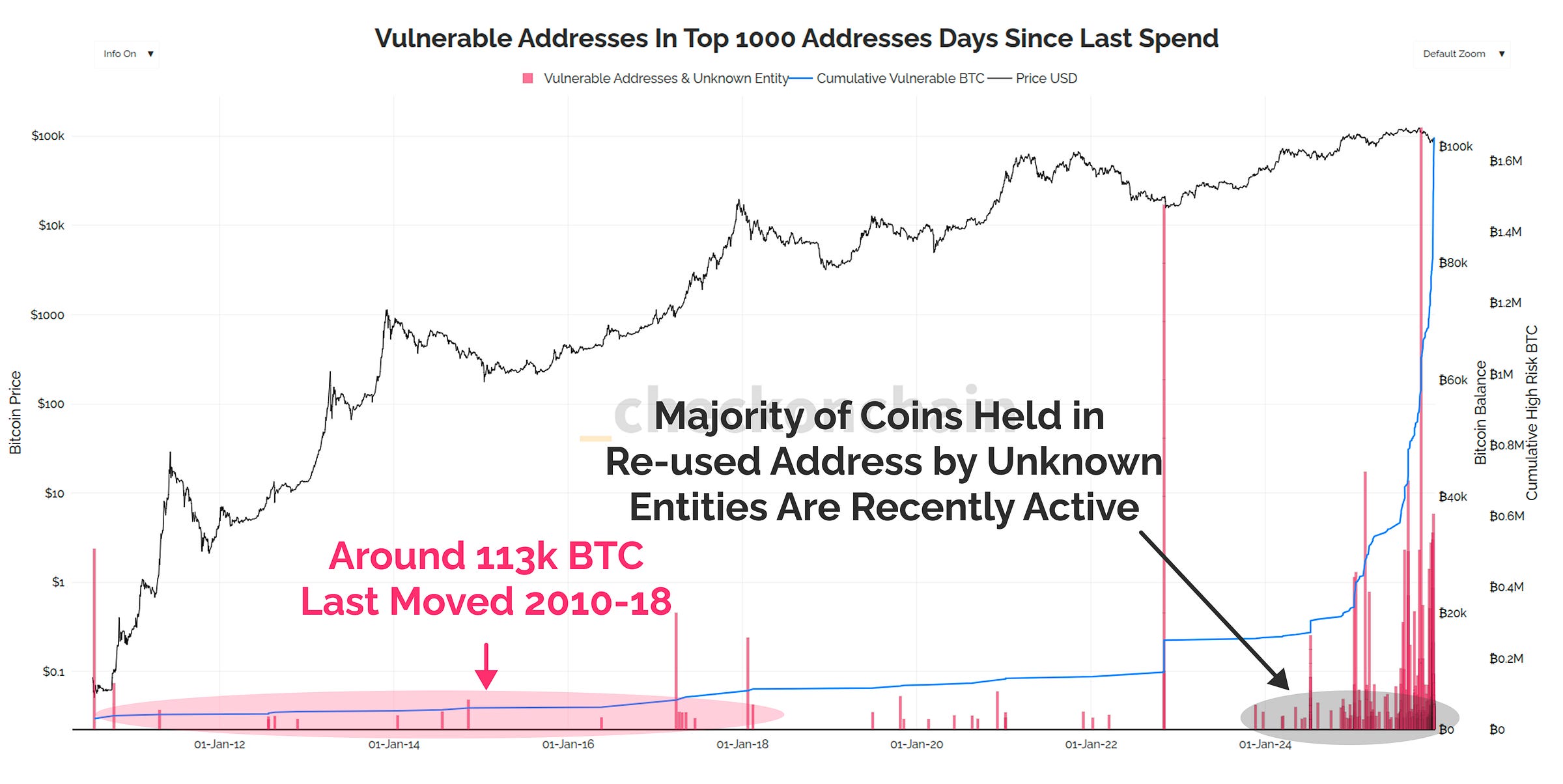
This picture gets even less extreme when we look at how recently these re-used addresses, held by unknown entities, have spent coins (signalling they are alive and unlikely to be lost).
The vast majority of the top 1000 re-used addresses are quite active, which indicates that the owner is capable, and likely to upgrade to quantum safe practices over time.
The final break-down or the top 1000 re-used addresses by risk is as follows:
🔵 Low Risk: 1.245M BTC (~$112B) held in re-used addresses, but owned by a labelled entity such as an exchange or custodian.
🟠 Moderate Risk: 1.553M BTC (~$140B) held in re-used addresses, without a corresponding entity label, but is actively spending since Feb-2018.
🔴 Highest Risk: 113k BTC (~$10B) held in re-used addresses, without an entity label, but has not transacted since Feb-2018, and thus may be lost.
Whilst address re-use is vulnerable to CRQC, and should be discouraged, my read here is the number of high risk BTC held in re-used addresses is unlikely to be a larger honeypot than the legacy Satoshi era coins.
This does not negate the user experience challenges that come with discouraging address re-use. Bitcoiners must work very hard on education, and upgrading wallet infrastructure to minimise address re-use as much as possible on the road ahead.
Vulnerable Supply Summary
This is by no means a complete analysis of the vulnerable coins, but there are a few key conclusions I think we can draw out:
There are 1.902 M BTC ($171B) held in vulnerable P2PK, P2MS or P2TR addresses.
The 1.720M BTC held in Satoshi Era P2PK addresses are the most at risk, since they are very likely lost, and are equivalent to a full year of bull market distribution pressure by 3-year+ coins.
My assumption is that many of the modern Taproot P2TR addresses are owned by active participants, who are also very likely to upgrade to quantum safe practices.
Address re-use is a big problem, with 2022 estimates showing around half of all UTXOs have a re-used address as their destination. This is very skewed towards exchanges and custodians, who have the capacity and incentive to upgrade their wallet management practices (albeit requiring difficult changes to user experience).
When we study the 29.5% of the circulating supply (5.896M BTC) held in the top 1000 Bitcoin ‘rich list’ addresses, around half are in vulnerable re-used addresses.
However, most of those wallets have spent coins in the last few years, suggesting the owner is either an exchange, a custodian, or a whale entity who is alive and active in the market.
The highest risk category are the 113k BTC held in unlabelled and dormant re-used addresses, which are more likely to be lost.
If we extrapolate this relative proportion of this high risk category to the entire Bitcoin supply, we can get a very crude estimate of lost coins in vulnerable re-used addresses.
We have 133k BTC out of 5.896M in the top 1000 that are high risk (1.91% of the rich list). Applying a similar ratio, we could consider say 2% to 5% of the global Bitcoin supply (minus P2PK coins), giving us a vulnerable lost and in re-used address supply range of:
Globally, this would indicate the total CRQC vulnerable supply held in addresses that are likely lost, amounts to between 2.08M ($187B) and 2.63M ($237B) BTC.
For comparison, this is approximately three and a half Strategy Treasuries that are vulnerable, and unlikely to upgrade to a quantum safe setup.
What Do We Do About Lost & Vulnerable Coins?
This is one of the most interesting parts of the quantum debate, and there is a very sound case to be made for both solution pathways:
The Burn Option: As a network, we agree to a consensus change which freezes, burns, or makes otherwise unspendable all vulnerable coins after a particular block-height before the arrival of ‘Q-day’. The underlying principle is that if we allow a malicious QC attacker to violate the cryptographic security of Bitcoin, the market will lose trust in the system as a whole. There is a valid position that the owner of lost and vulnerable coins probably doesn’t want anyone else to have access to them either.
The Jungle Option: The law of the jungle is that we do nothing, and these vulnerable coins are fair game for whomever has access to the private key (whether honestly, or by theft, by robbery, or a quantum break). The underlying principle is that Bitcoin enshrines property rights, and our collective burning of other people’s coins is a violation of that core tenant of self-sovereignty. Once we set a precedent that the network can confiscate the property of others, it becomes difficult to trust that it won’t happen again in the future.
The first thing to note, is that the Jungle Option is both the default, and in my honest opinion, the most likely outcome. I find it very difficult to believe we will ever achieve the requisite overwhelming consensus for a Bitcoin soft (or hard) fork to burn coins. The engineer in me looks at this problem, and believes the pragmatic reality is that those coins will inevitably be claimed by a CRQC.
Personally, I am a Jungle guy, because if someone opts not to upgrade their coins, that was their choice. If we burn coins, we have made that choice for them.
I am of the view that the primary reason people do not want the Jungle Option is because they fear the impact to the price, which is an inherently self-focused (but very understandable) viewpoint. I do not think price is a Bitcoin consensus issue, and all consensus changes should seek to preserve the ‘idea’ that Bitcoin represents, self-sovereignty over money.
The price can recover, but the signal sent by burning someone else’s coins, and demonstrating that your coins are actually our coins…is irreversible.
There is also the question about how we encode a rule that defines a coin as ‘lost’. We have already seen 80k BTC from 2011 come back to market this cycle, and any rational thinker would have assumed them to have been lost.
The Man In The Coma
Imagine Hal Finney is in fact Satoshi. Hal had his body cryogenically frozen in the hope that future medical advances would find a cure for his ALS disease.
We as the Bitcoin network decide to freeze all P2PK coins on 1-Jan-2030 out of fear that Q-day is close (assume it is expected in 2035).
Modern medical technology, powered by AI, and maybe even state-of-the-art quantum computing finds a cure for ALS, and successfully revives Hal in Jan-2031…
…and what if Q-day never actually comes? Or the US Government was destined to be the one that takes the coins and has a system in place to reclaim them given private key proof?
Quite the moral dilemma.
The more I ponder this dilemma, the more I find myself on the side of the Jungle Option, because it protects the irreplaceable ‘idea’ of Bitcoin as a system where you have the choice, even if that choice is to NOT protect your Bitcoin holdings.
Quantum Actors
The other side-bar, is we need to consider who the most likely actor to achieve the first CRQC will be, and what their incentives are.
In my opinion, it will most likely be:
A high flying tech company like Google, Microsoft, IBM etc.
The US government, or some entity they have jurisdiction over.
The Chinese government, or some entity they have jurisdiction over.
In the first two instances, I highly doubt IBM or the USG would seek to market dump 2M stolen coins on Coinbase. Whilst a higher risk, I also don’t think the Chinese government would do this as it would drastically sour international relations.
We can never know who ends up with the first CRQC, but I do believe the odds are quite high it would end up being some benevolent dictator with government involvement. The coins, if stolen at all, would likely end up in a government reserve somewhere, and be retrievable via the legal system should proof of original ownership is provided (trivially shown by signing a message with the source private key).
The Hourglass Idea
The last topic we need to touch on is how long it will take the market to migrate to a post-quantum safe address format, once it is ready.
It will take several years to debate, design, implement, and coordinate a soft fork that installs quantum safe address formats for Bitcoin.
It will then likely take more than 1yr of full blocks for users to migrate their holdings over to these quantum safe addresses, and that doesn’t even factor in day-to-day network traffic!
This is why we need to start thinking about quantum safe addresses now.
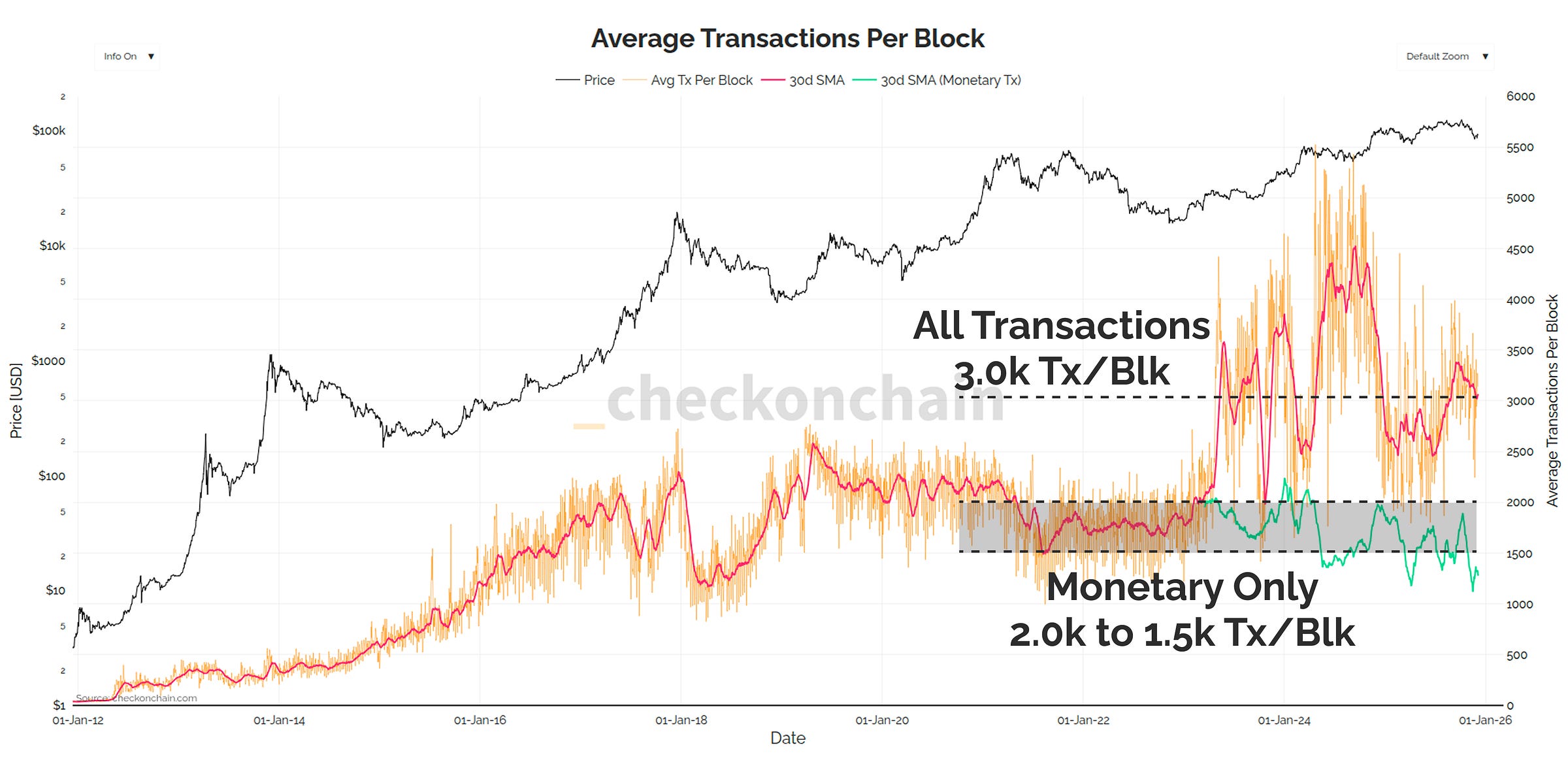
On average, the Bitcoin network fits around 3,000 transactions in a block. This is partly skewed higher due to inscriptions which take advantage of the witness discount.
Purely monetary transactions see between 1,500 and 2,000 transactions per block on average.
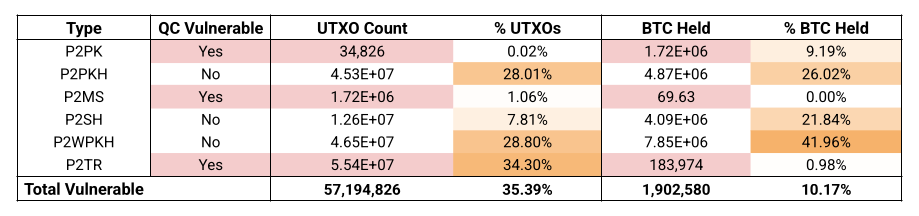
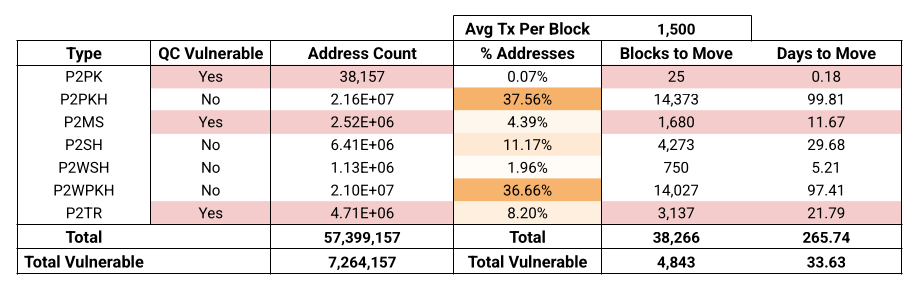
The table below shows the 57M addresses which hold some amount of BTC across the Bitcoin network, broken down into address types.
Assuming perfect conditions, and zero network day-to-day traffic, it would take 265-days to migrate each existing address to a new quantum safe address.
The majority (74%) of the network is held in P2PKH (Legacy ‘1’) and P2WPKH (SegWit ‘bc1q’) addresses, both of which are quantum safe so long as the user does not re-use addresses, and keeps their xpub safe.
Nevertheless, the logistical challenge, and time required for a full migration of the Bitcoin network is non-trivial, and requires significant effort over the coming years.
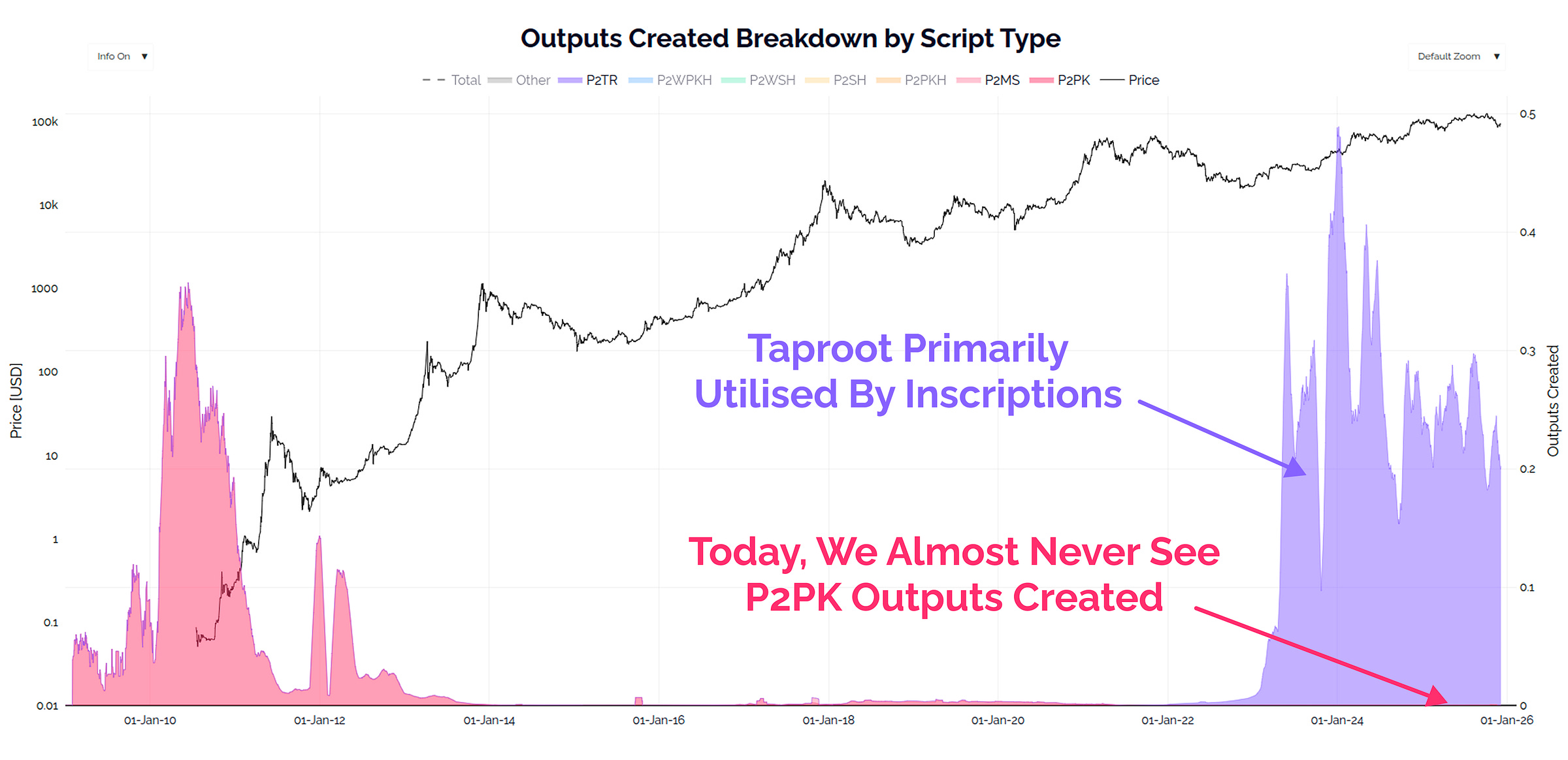
As we already know, the most vulnerable coins are those which are lost, and thus unlikely to upgrade. The 1.72M BTC in Satoshi era P2PK addresses are the largest honeypot at risk, but they have also been deprecated for many years, and we rarely see a single P2PK coin spent for weeks, months, and even years at a time.
The default, is that P2PK coins are almost never spent today, with only a few hundred of them moving since 2023.
The vast majority of activity on the Bitcoin network today comes from modern address formats like SegWit (blue) and Taproot (purple).
One proposal that I think is quite intriguing, is called the Hourglass method, where instead of freezing P2PK coins, we instead ‘rate-limit’ their spending.
A consensus rule could be established that only allowed miners to include one P2PK spend per block. The idea is that if a CRQC did crack the cryptography, they would only be able to steal one ~50BTC lot every 10-mins, almost like a new block reward.
There is also the concept that if there are two competing CRQCs, both would try to steam the coins, and would have to continuously bump up the transaction fee, which would progressively eat into the prize, and ultimately pay most of this back to miners.
Given there are 38,157 P2PK addresses, with the hourglass method, it would take 264-days for all the vulnerable coins to be consumed with one P2PK spend per block.
This is approximately on the same time-span it would take the rest of the network, and would also act as a ‘canary in the coal-mine’, where Q-Day would be revealed when P2PK coins start being moved. The earliest CRQCs will likely take more than 10-mins to reverse engineer a private key, so we would see a slow drip of theft at first, but it would speed up as the technology improved.
In Bitcoin, and indeed in life, there are no solutions, only trade-offs.
The hourglass approach is an interesting one, which I think meets in the middle of the law of the Jungle, and the option to burn coins.
Important note: I am also of the view that the development and release of full quantum-safe address formats, is a separate and much more important decision tree than the burning/rate-limit of coins.
We must first give people the tools to upgrade.
Then we can debate what happens to the vulnerable coins which don’t.
I suspect we will be surprised by how many of the assumed ‘lost coins’ are actually just in deep cold storage, and come back to life through this process.
Concluding Thoughts
This was a very quantum-cross-Bitcoin jargon heavy piece. You can probably see why it has taken me several months to compile my thoughts on it.
Let me summarise the essential take-away messages:
The quantum threat to Bitcoin is hard to handicap, but I am seeing enough smart and credible people suggesting it is real, and likely on the horizon for the next decade (Q-day somewhere in 2030-2035).
The majority of Bitcoin is currently quantum safe, and the coins you hold in your wallet will not be vulnerable to theft assuming the following:
You do not re-use addresses, and treat all addresses as one-time-use (if you do re-use, it is time to upgrade your security practices). Most wallets already generate a new address for you by default, making it standard practice.
Your coins are held in modern SegWit addresses starting with ‘bc1q’. Technically speaking older legacy addresses starting with ‘3’ are safe too, but most wallet software has deprecated these formats.
There are three main buckets of coins vulnerable to quantum theft:
1.72M BTC in Satoshi Era P2PK addresses, which are very likely lost, and thus at a high risk of quantum theft.
184k BTC in modern Taproot addresses, which is 1% of the supply, but the owners are likely to be active and can therefore upgrade.
I estimate 2% to 5% of the supply (365k to 914k BTC) is held in re-used addresses that are likely to be lost and unable to upgrade.
There is a much larger pool of 2.798M BTC in re-used addresses, however these are either active, or associated with exchanges and custodians. In both instances, the owning entity has the capacity to upgrade to quantum-safe practices over time.
Globally, I estimate there are between 2.08M ($187B) and 2.63M ($237B) vulnerable and lost BTC, equivalent to 3x to 4x Strategy Treasuries.
There is also a debate around whether we freeze/burn these vulnerable coins, or allow the law of the jungle to apply. Both have valid principles as the foundation, however I find myself opposed to the burning idea. I am much more in favour of a rate-limiting hourglass approach that constrains the movement of P2PK coins to say 1-per-block (in line with the rest of the upgrade timeline, and much more than actual daily spends today).
We have not even made it into a discussion of the quantum safe address formats which are being proposed!
I would encourage those interested to read through BIP-360, which I find compelling as a solution, even though I am far too dumb to understand any of the inner workings.
The quantum threat is one I believe we need to take seriously, but I do not believe we need to panic about it. We have time, we have smart engineers, and the solution starts with having the conversation now, so we are well prepared for the future.
I have a high degree of confidence that Bitcoiners will solve this problem, simply, because our life savings may depend on it.
Thanks for reading,
James